Windows 2006 Server has some interesting features that I would like to mentions:
1. Nested virtualization feature that it mean you can run Hyper-V inside of a Virtual Machine (VM). Hyper-V host can itself be virtualized and so very useful for testing purpose.
2. Shielded virtual machine, you can review this blog article too, the major concept to avoid VM steal:
http://www.alessandromazzanti.com/2017/03/windows-server-2016-deploying-shielded.html
3. Hot Adding Hyper-V Network Adapters and Memory without reboot necessity.
4. Cluster upgrade path from 2012 R2 to 2016 - If you have cluster nodes Windows 2012 R2 you can slowing upgrade to windows 2016 server mantaining cluster in mixed mode and finally using the command powershell (not revirsible)
Update-ClusterFunctionalLevel
4. Windows Server 2016 introduce Cluster Azure Cloud Witness too.
5. Site-aware Failover Clusters At the same time cluster groups server based on site geographical location.
Site-aware Failover Clusters in Windows Server 2016.
cluster-whiteness-cloud-configuration
Workgroup e Multi-domain Cluster on 2016 override 2012 R2 limitations that all cluster servers member need to be all located in same AD site.
6. Diagnostic in Failover Clustering is enhanced than in the past, you can review these articles:
Windows Server 2016 Failover Cluster Troubleshooting Enhancements – Cluster Log
Windows Server 2016 Failover Cluster Troubleshooting Enhancements – Active Dump
7. SMB Multichannel e Multi-NIC Cluster Network
https://technet.microsoft.com/en-us/windows-server-docs/failover-clustering/smb-multichannel
[Reference article]
https://www.backupassist.com/blog/news/what-to-look-forward-to-in-windows-server-2016/
Pagine
▼
USB - how to create LIVE installation USB with Vmware 6.5
If you need to create an USB installation key with Vmware 6.5 you simple need to have:
Vmware 6.5 ISO download
Netbootin ISO to USB tool download
Once you have download .iso you need to put Netbootin link to usb as following image and proceed with USB creation.

about USB and CD tools you can review these blogs sections:
http://www.alessandromazzanti.com/search/label/CD%20Live
http://www.alessandromazzanti.com/search/label/USB
Vmware 6.5 ISO download
Netbootin ISO to USB tool download
Once you have download .iso you need to put Netbootin link to usb as following image and proceed with USB creation.
about USB and CD tools you can review these blogs sections:
http://www.alessandromazzanti.com/search/label/CD%20Live
http://www.alessandromazzanti.com/search/label/USB
Alessandro M.
Monitoring - Naemon Monitoring Server
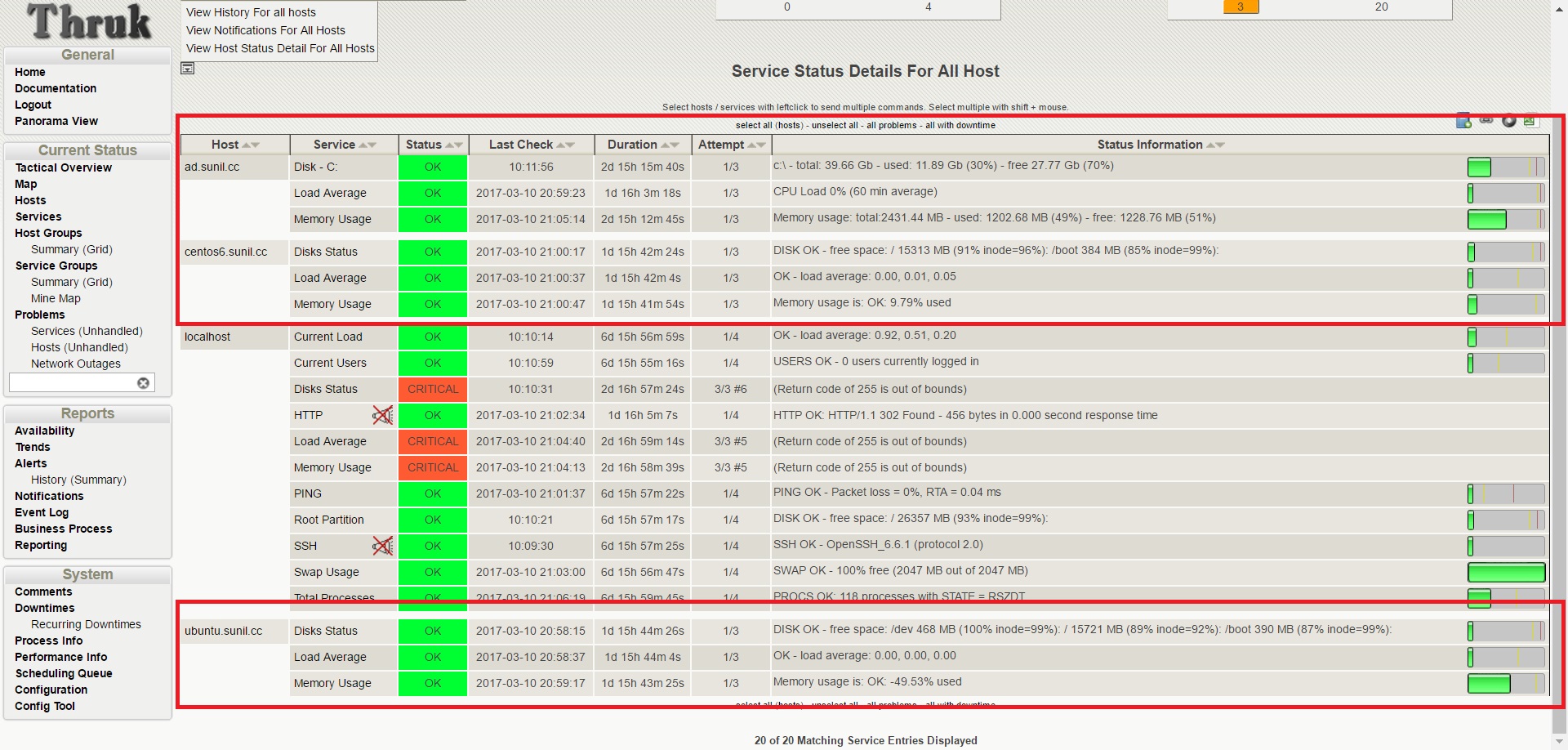
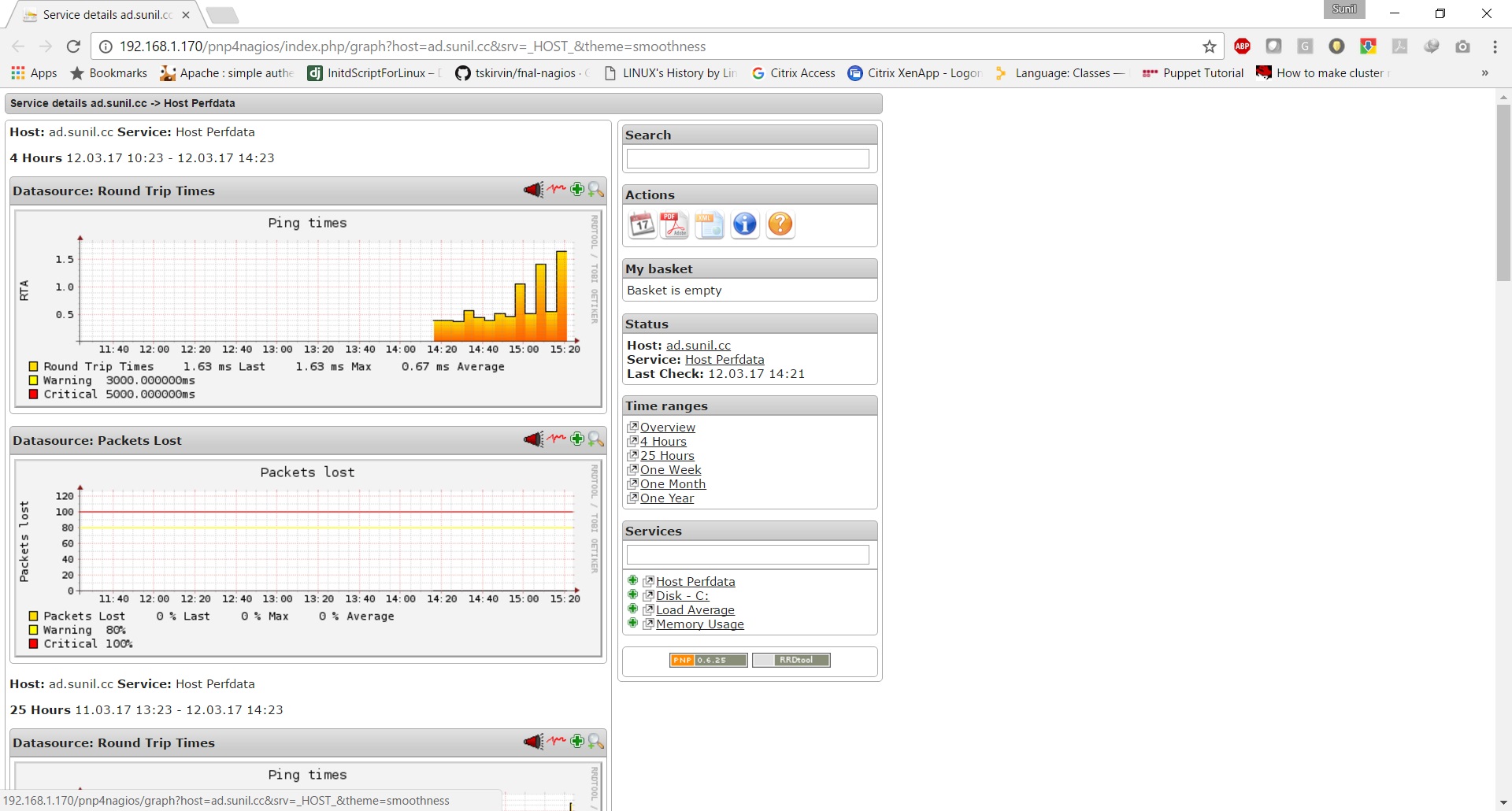
Naemon is new monitoring suite that permit to give you a clear view of the state of your network and applications.
This is a replacement for nagios server, stable and that uses a dashboard called thruk.
Here it a tutorial that will use four Servers
192.168.1.170 - Naemon Server - centos 7
192.168.1.21 - nrpe client - centos 6
192.168.1.182 - nrpe client - ubuntu
192.168.1.75 - nscp client - windows server 2012R2
Tutorial
https://www.howtoforge.com/tutorial/how-to-install-a-production-ready-naemon-server/
This is a replacement for nagios server, stable and that uses a dashboard called thruk.
Here it a tutorial that will use four Servers
192.168.1.170 - Naemon Server - centos 7
192.168.1.21 - nrpe client - centos 6
192.168.1.182 - nrpe client - ubuntu
192.168.1.75 - nscp client - windows server 2012R2
Tutorial
https://www.howtoforge.com/tutorial/how-to-install-a-production-ready-naemon-server/


Alessandro M.
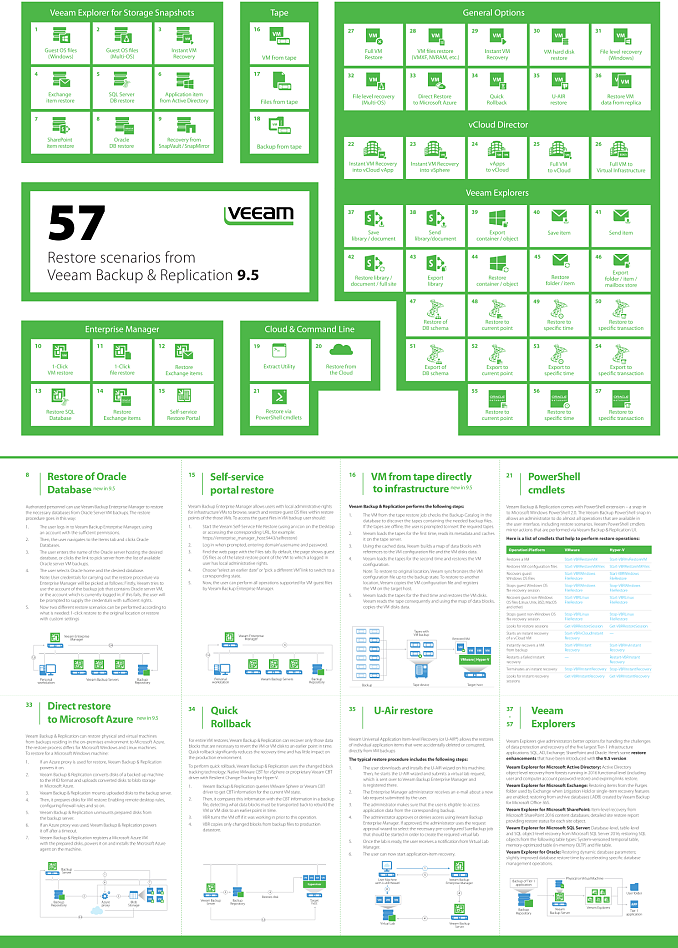
Veeam - 57 restore scenario
Today I would like to mention a nice Veeam PDF that enumerate, in a single page, 57 restore scenario supported.
https://www.veeam.com/pdf/datasheet/57_veeam_restore_scenarios_A0.pdf
the poster is available in A0, A1 and A2 formats.
https://www.veeam.com/pdf/datasheet/57_veeam_restore_scenarios_A0.pdf
the poster is available in A0, A1 and A2 formats.

Alessandro M.
Hacker - Ransomware CryptON decryptor tools
Here they are some decrypter tools about CryptON ramsomware.
1.) Emisoft tool can be directely downloaded from this link
https://decrypter.emsisoft.com/download/crypton
Step by step procedure can be found here.
https://www.bleepingcomputer.com/news/security/emsisoft-releases-a-decryptor-for-the-crypton-ransomware/
In any case you should drag and drop encrypted files to .exe tool.
After that you will find decryting key (after a while)
Once finished you will prompted about license acceptance windows and then for adding files/folder that you have decrypting necessity.
2.) Kaspersky decrypter
http://media.kaspersky.com/utilities/VirusUtilities/EN/rakhnidecryptor.zip
3.) Eset decrypter
https://download.eset.com/com/eset/tools/decryptors/crysis/latest/esetcrysisdecryptor.exe
1.) Emisoft tool can be directely downloaded from this link
https://decrypter.emsisoft.com/download/crypton
Step by step procedure can be found here.
https://www.bleepingcomputer.com/news/security/emsisoft-releases-a-decryptor-for-the-crypton-ransomware/
In any case you should drag and drop encrypted files to .exe tool.
After that you will find decryting key (after a while)
Once finished you will prompted about license acceptance windows and then for adding files/folder that you have decrypting necessity.
2.) Kaspersky decrypter
http://media.kaspersky.com/utilities/VirusUtilities/EN/rakhnidecryptor.zip
3.) Eset decrypter
https://download.eset.com/com/eset/tools/decryptors/crysis/latest/esetcrysisdecryptor.exe
Alessandro M.
Linux - How to install MS SQL and .NET on several Linux distributions
Microsoft released SQL version that can be installed on Linux environment.
Here they are more details with step by step installation guides
Microsoft started with .NET and now SQL, I guess their mantra now is “if you can’t beat them, join them..."
About .NET on linux you can quickly review this base Microsoft article:
https://www.microsoft.com/net/core#linuxredhat
https://docs.microsoft.com/en-us/aspnet/core/publishing/linuxproduction
indeed about SQL on Linux:
More information can be found here:
SQL Server on Linux Documentation
Here they are more details with step by step installation guides
Microsoft started with .NET and now SQL, I guess their mantra now is “if you can’t beat them, join them..."
About .NET on linux you can quickly review this base Microsoft article:
https://www.microsoft.com/net/core#linuxredhat
https://docs.microsoft.com/en-us/aspnet/core/publishing/linuxproduction
indeed about SQL on Linux:
CTP 1.4 (March 2017)
Supported platforms
| Platform | File System | Installation Guide |
|---|---|---|
| Red Hat Enterprise Linux 7.3 Workstation, Server, and Desktop | XFS or EXT4 | Installation guide |
| SUSE Enterprise Linux Server v12 SP2 | EXT4 | Installation guide |
| Ubuntu 16.04LTS and 16.10 | EXT4 | Installation guide |
| Docker Engine 1.8+ on Windows, Mac, or Linux | N/A | Installation guide |
More information can be found here:
SQL Server on Linux Documentation
Alessandro M.
Apple - Song Sleuth
Several persons used Shazam app that permit to recognize songs name and singers simple listening unknown musi.
I discovered that now exist an app that permit to recognize birds simple listening to their chants.
For the moment it is only for ipad/iphone and it is not for free:
Here it is a more verbosely explanation:
"Song Sleuth turns your iPhone or iPad into an automatic bird song identifier covering the 200 most common vocalizing land birds in the U.S. Developed by Wildlife Acoustics, in collaboration with world-renowned bird expert and illustrator David Sibley, the app records bird songs and suggests likely matching species. The identification algorithms are the result of over a decade of research and experience designing professional bioacoustics recorders and software.
Not just for beginners, the app also has features for intermediate birders who might need an identification hint or wish to study the included example recordings to take their ear birding to the next level. Advanced birders who don’t need any identification help will appreciate the ability to make and keep recordings for further study."
Alessandro M.
Windows 2012 - Deduplication
Windows 2012 has built in deduplication feature.
This permit you to save space.
I you want to add this feature you need, from dashboard:
This permit you to save space.
I you want to add this feature you need, from dashboard:
- Add roles and features --> Role based…--> Next
- File and Storage Services --> File and Storage Services --> File and iSCSI services --> Data deduplication.
- After that you can proceed to configure a share folder or a drive with deduplication scheduling when job should work during off working hours
https://blogs.technet.microsoft.com/filecab/2012/05/20/introduction-to-data-deduplication-in-windows-server-2012/
Consider that deduplication feauture is decisevely interesting if applied to HyperV VM(.vhd-.vhdx) to save space.
Here is an italian article that well explain in any case, with W2012 R2 when you are going to create e new VM you will see this option too.
Virtual Desktop Infrastructure (VDI) server

https://www.achab.it/achab.cfm/it/blog/achablog/risparmiare-spazio-disco-con-la-deduplica-delle-macchine-virtuali-di-hyper-v
Consider that deduplication feauture is decisevely interesting if applied to HyperV VM(.vhd-.vhdx) to save space.
Here is an italian article that well explain in any case, with W2012 R2 when you are going to create e new VM you will see this option too.
Virtual Desktop Infrastructure (VDI) server

https://www.achab.it/achab.cfm/it/blog/achablog/risparmiare-spazio-disco-con-la-deduplica-delle-macchine-virtuali-di-hyper-v
Alessandro M.
Windows Server 2016 - Deploying Shielded VMs and a Guarded Fabric
Imagine that someone manages to walk out the door with dozens of virtual machines because they’re all centrally located. Worse, they can take those virtual machines home and run them on their personal desktop or laptop and you still have no idea they left the premises.
Finally :
Safeguard VMs so that VMs can only run on infrastructure you designate as your organization’s fabric and are
Protected VMs even from compromised administrators.
To do this, we are introducing Shielded VMs in Windows Server 2016. Shielded VMs protect virtual machines from compromised or malicious administrators in the fabric, such as storage admins, backup admins, etc. by encrypting disk and state of virtual machines so only VM or tenant admins can access it.
In addition, we are also protecting the fabric with a new Windows Server feature: the Host Guardian Service. When a shielded virtual machine is turned on, the Host Guardian Service (HGS) checks to see if the hosts are allowed to run the Shielded VM. This is accomplished through attestation and hardware based boot measurements along with a new feature: Code integrity to determine whether a host meets the criteria as a healthy host and may run the Shielded VM.
Here it MVA video courses that explain how deploying Shielded VMs and a Guarded Fabric with Windows Server 2016
More details:
A closer look at shielded VMs in Windows Server 2016
Guarded fabric and shielded VMs overview
Shielded VMs documentation
Shielded VMs infographic
<------------->
Here it is an interesting Microsoft Video about how securing VMs on 2016.
https://mva.microsoft.com/en-US/training-courses/deploying-shielded-vms-and-a-guarded-fabric-with-windows-server-2016-17131?l=WFLef7vUD_4604300474
MVA Course:
Wondering what it takes to go from a Windows Server 2012 fabric to a Windows Server 2016 guarded fabric? Need help setting up that guarded fabric? In this hour-long course, join experts for an end-to-end step-through of a live Windows Server 2016 guarded fabric deployment—hands-on, brick by brick. See how easy it is, with the right hardware and software, to set up this security.
Start with a look at the Host Guardian Service (HGS), and then learn to configure Trusted Platform Module–based (TPM-based) attestation on the Hyper-V host. Create baseline security policies and Hypervisor-enforced Code Integrity policies, and configure HGS to attest to them. Plus, get the details on signing trustworthy template disks, creating shielding data, and deploying Shielded VMs.
NOTE: If you need a refresher, take a look at Ryan Puffer’s Windows IT Center entry on guarded fabric and Shielded VMs and at the Datacenter and Private Cloud Security Blog.
Finally :
Safeguard VMs so that VMs can only run on infrastructure you designate as your organization’s fabric and are
Protected VMs even from compromised administrators.
To do this, we are introducing Shielded VMs in Windows Server 2016. Shielded VMs protect virtual machines from compromised or malicious administrators in the fabric, such as storage admins, backup admins, etc. by encrypting disk and state of virtual machines so only VM or tenant admins can access it.
In addition, we are also protecting the fabric with a new Windows Server feature: the Host Guardian Service. When a shielded virtual machine is turned on, the Host Guardian Service (HGS) checks to see if the hosts are allowed to run the Shielded VM. This is accomplished through attestation and hardware based boot measurements along with a new feature: Code integrity to determine whether a host meets the criteria as a healthy host and may run the Shielded VM.
Here it MVA video courses that explain how deploying Shielded VMs and a Guarded Fabric with Windows Server 2016
More details:
A closer look at shielded VMs in Windows Server 2016
Guarded fabric and shielded VMs overview
Shielded VMs documentation
Shielded VMs infographic
<------------->
Here it is an interesting Microsoft Video about how securing VMs on 2016.
https://mva.microsoft.com/en-US/training-courses/deploying-shielded-vms-and-a-guarded-fabric-with-windows-server-2016-17131?l=WFLef7vUD_4604300474
MVA Course:
Wondering what it takes to go from a Windows Server 2012 fabric to a Windows Server 2016 guarded fabric? Need help setting up that guarded fabric? In this hour-long course, join experts for an end-to-end step-through of a live Windows Server 2016 guarded fabric deployment—hands-on, brick by brick. See how easy it is, with the right hardware and software, to set up this security.
1 | Deploying Shielded VMs in a Windows Server 2016 Guarded Fabric
Get an in-depth look at a live deployment of a Windows Server 2016 guarded fabric—hands-on, brick-by-brick, from the ground up.
Alessandro M.
Tips - User logon with temporary user
If you are facing user that logon to pc/server but with temporary profile you simple need to :
- Logon with different administrator user
- regedit and going to section:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList - Select profile name with .bak extention and renaming it to .old
Alessandro M.
Tool - MD5 calculation
Here they are some tools that permit to calculate MD5:
1. Fastsum: http://www.fastsum.com/
2. WinMD5Free: http://www.winmd5.com/
3. If you need to calculate CRC you can use this Microsoft tool (FCIV)
1. Fastsum: http://www.fastsum.com/
2. WinMD5Free: http://www.winmd5.com/
3. If you need to calculate CRC you can use this Microsoft tool (FCIV)
Here is a syntax example but you could obviously use a different syntax
Get-ChildItem C:\Scripts, C:\Test, "C:\Documents and Settings\Kenmyer\Desktop" -filter "*.ps1"
If you like to go deeper on MD5 theory you can review wikipedia article:
If you like to go deeper on MD5 theory you can review wikipedia article:
The MD5 algorithm is a widely used hash function producing a 128-bit hash value. Although MD5 was initially designed to be used as a cryptographic hash function, it has been found to suffer from extensive vulnerabilities. It can still be used as a checksum to verify data integrity, but only against unintentional corruption.
Like most hash functions, MD5 is neither encryption nor encoding. It can be cracked by brute-force attack and suffers from extensive vulnerabilities as detailed in the security section below.
MD5 was designed by Ronald Rivest in 1991 to replace an earlier hash function MD4.[3] The source code in RFC 1321 contains a "by attribution" RSA license. The acronym "MD" stands for "Message Digest."
The security of the MD5 has been severely compromised, with its weaknesses having been exploited in the field, most infamously by the Flame malware in 2012. The CMU Software Engineering Institute considers MD5 essentially "cryptographically broken and unsuitable for further use".[4]
Alessandro M.
Windows 10 - How to manage updates
Today I would like to highlith these Microsoft articles that explain how to manage Windows 10 updates as a service.
Unfortunately they are in italian language but could be easily translated on line to any preferred language.
https://technet.microsoft.com/it-it/itpro/windows/manage/waas-update-windows-10?wt.mc_id=AID521892_EML_4912522
Unfortunately they are in italian language but could be easily translated on line to any preferred language.
https://technet.microsoft.com/it-it/itpro/windows/manage/waas-update-windows-10?wt.mc_id=AID521892_EML_4912522
| Argomento | Descrizione |
|---|---|
| Guida rapida a Windows as a Service | Fornisce un breve riepilogo dei punti principali relativi al nuovo modello di manutenzione per Windows 10. |
| Panoramica di Windows as a Service | Spiega le differenze in termini di compilazione, distribuzione e manutenzione di Windows 10, presenta gli aggiornamenti delle funzionalità, gli aggiornamenti qualitativi e i diversi rami di manutenzione e confronta gli strumenti di manutenzione. |
| Preparare la strategia di manutenzione per gli aggiornamenti di Windows 10 | Illustra le decisioni da prendere nella strategia di manutenzione. |
| Creare circuiti di distribuzione per gli aggiornamenti di Windows 10 | Spiega come usare i rami di manutenzione e i rinvii degli aggiornamenti per gestire gli aggiornamenti di Windows 10. |
| Assegnare i dispositivi ai rami di manutenzione per gli aggiornamenti di Windows 10 | Spiega come assegnare dispositivi al ramo CB (Current Branch) o CBB (Branch for Business) per gli aggiornamenti qualitativi e delle funzionalità e come registrare dispositivi in Windows Insider. |
| Ottimizzare il recapito degli aggiornamenti di Windows 10 | Illustra i vantaggi dell'uso di Ottimizzazione recapito o BranchCache per la distribuzione degli aggiornamenti. |
| Gestire gli aggiornamenti per Windows 10 Mobile Enterprise e Windows 10 IoT Mobile | Descrive gli aggiornamenti per Windows 10 Mobile Enterprise e Windows 10 IoT Mobile. |
| Gestire gli aggiornamenti con Windows Update for Business | Spiega come usare Windows Update for Business per gestire quando i dispositivi ricevono gli aggiornamenti direttamente da Windows Update. Include procedure dettagliate per configurare Windows Update for Business tramite Criteri di gruppo e Microsoft Intune. |
| Gestire gli aggiornamenti di Windows 10 con Windows Server Update Services (WSUS) | Spiega come usare WSUS per gestire gli aggiornamenti di Windows 10. |
| Gestire gli aggiornamenti di Windows 10 con System Center Configuration Manager | Spiega come usare Configuration Manager per gestire gli aggiornamenti di Windows 10. |
| Gestire i riavvii dei dispositivi dopo gli aggiornamenti | Spiega come usare Criteri di gruppo per gestire i riavvii dei dispositivi. |
Alessandro M.
