http://hultbergs.org/defrag/
MS Dos - Defrag during MS dos period
Here is simple link that let us to review Windows 95 defrag process and relative HD sound:
http://hultbergs.org/defrag/
http://hultbergs.org/defrag/
Extra IT - Gag/Funny web site
Today I would like to mention this funny website with several gags and amazing argument.
Have a funny.
https://www.reddit.com/r/funny/
Have a funny.
https://www.reddit.com/r/funny/
Labels:
Extra IT
Tuning - Windows uninstalling clean up utility
I found an interesting utility that help to cleanup registry/windows settings after a software uninstallation that went not as expected.
Here it is relative link and explanations:
http://it.ccm.net/download/scaricare-434-windows-installer-cleanup-utility
Here it is relative link and explanations:
http://it.ccm.net/download/scaricare-434-windows-installer-cleanup-utility
Labels:
Freeware,
Manutenzione,
Programs,
Tips,
tuning
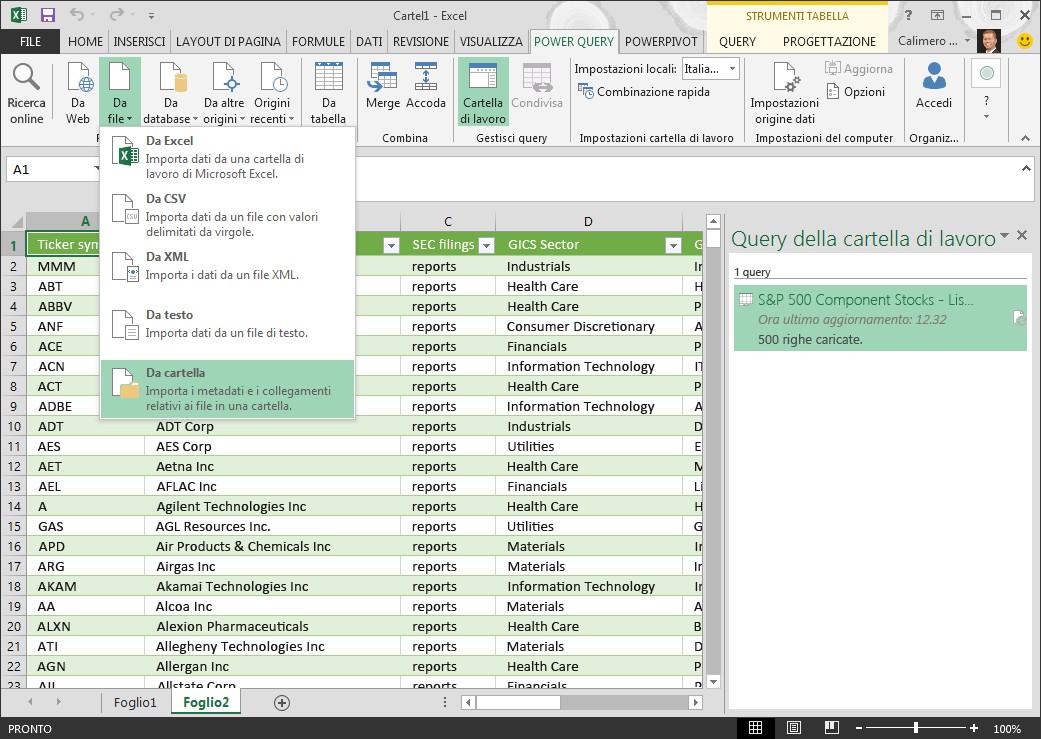
Microsoft Power Query for Excel
Microsoft Power Query for Excel is an Excel add-in that enhances the self-service Business Intelligence experience in Excel by simplifying data discovery, access and collaboration.
i would like to highlight this excel tool that i recently discovered
download:
https://www.microsoft.com/en-us/download/details.aspx?id=39379&CorrelationId=c2276676-6a86-4e6d-9722-be34ed96503e
Power Query enhances self-service business intelligence (BI) for Excel with an intuitive and consistent experience for discovering, combining, and refining data across a wide variety of sources including relational, structured and semi-structured, OData, Web, Hadoop, and more.
If you want to go deeper with this tool you can review these articles:
https://www.excelcampus.com/powerquery/power-query-overview/
Power Query italian & English Guide
https://support.office.com/it-it/article/Guida-di-Microsoft-Power-Query-per-Excel-2b433a85-ddfb-420b-9cda-fe0e60b82a94?CorrelationId=44f59a8b-1551-4bc2-86e5-59f17fd0cf64&ui=it-IT&rs=it-IT&ad=IT
https://support.office.com/en-us/article/Introduction-to-Microsoft-Power-Query-for-Excel-6E92E2F4-2079-4E1F-BAD5-89F6269CD605
Power Query M function reference
https://msdn.microsoft.com/library/1ed840b1-7e20-4419-ad2f-d82054c9b2ab
Power Query M Reference
https://msdn.microsoft.com/en-us/library/mt211003.aspx
i would like to highlight this excel tool that i recently discovered
download:
https://www.microsoft.com/en-us/download/details.aspx?id=39379&CorrelationId=c2276676-6a86-4e6d-9722-be34ed96503e
Power Query enhances self-service business intelligence (BI) for Excel with an intuitive and consistent experience for discovering, combining, and refining data across a wide variety of sources including relational, structured and semi-structured, OData, Web, Hadoop, and more.
If you want to go deeper with this tool you can review these articles:
https://www.excelcampus.com/powerquery/power-query-overview/
Power Query italian & English Guide
https://support.office.com/it-it/article/Guida-di-Microsoft-Power-Query-per-Excel-2b433a85-ddfb-420b-9cda-fe0e60b82a94?CorrelationId=44f59a8b-1551-4bc2-86e5-59f17fd0cf64&ui=it-IT&rs=it-IT&ad=IT
https://support.office.com/en-us/article/Introduction-to-Microsoft-Power-Query-for-Excel-6E92E2F4-2079-4E1F-BAD5-89F6269CD605
Power Query M function reference
https://msdn.microsoft.com/library/1ed840b1-7e20-4419-ad2f-d82054c9b2ab
Power Query M Reference
https://msdn.microsoft.com/en-us/library/mt211003.aspx

Windows Server 2016 Breach Resistance for Your Operating System and Applications
Here it is an interesting MVA video that discuss how 2016 help against Breach Resistance
https://mva.microsoft.com/en-US/training-courses/windows-server-2016-breach-resistance-for-your-operating-system-and-applications-17265?l=IEKYswpbD_6104300474
https://mva.microsoft.com/en-US/training-courses/windows-server-2016-breach-resistance-for-your-operating-system-and-applications-17265?l=IEKYswpbD_6104300474
Labels:
Hacker,
Tutorial,
Windows 2016,
Windows 2016 Server
Windows 10 - Convert MBR to GPT
|
Labels:
Windows 10
GPO - How to create local Administrator account using Group policies
If you want that all Pcs/server under same OU will have automatically created a new local Administrator account with a specified password you can do that creating a precise GPO.
I already tested procedure in the past and it worked fine (with centralized management):
I already tested procedure in the past and it worked fine (with centralized management):
- Launch Group Policy Management console --> "create a GPO...." --> Group Policy Editor
- Navigate to Computer Configuration\Preferences\Control Panel Settings\Local Users and Groups
- right clieck in blank area and select New --> Local User
- Action --> update
- User name --> testadmuser
- You can setting up other settings.
- Put testadmuser password
- you can repeat precedent procedure about Administrator Account (built-in),
If you like you can review this article too
http://www.dannyeckes.com/create-local-admin-group-policy-gpo/
I would like to highlight this article that clearly explain how to decrypt stored AD password for local administrator account using precedently GPO and how to enforce security with Microsoft Premier support.
https://blogs.technet.microsoft.com/askpfeplat/2014/05/18/how-to-automate-changing-the-local-administrator-password/
I would like to highlight this article that clearly explain how to decrypt stored AD password for local administrator account using precedently GPO and how to enforce security with Microsoft Premier support.
https://blogs.technet.microsoft.com/askpfeplat/2014/05/18/how-to-automate-changing-the-local-administrator-password/
[update 2024.05.24]
in case you need to add an AD user Administrators members group you need to follow these steps
1. Launch Group Policy Management console --> "create a GPO...." --> Group Policy Editor
2. Navigate to Computer Configuration\Preferences\Control Panel Settings\Local Users and Groups
3. right clieck in blank area and select New --> Local Group
4. Action --> update
5. Group name --> Administrators (built-in)
6. You can setting up other settings.
7. Members, Add --> Search for the Service Account in AD
8. Action--> Add to this group
Veeam - Incremental vs. differential methods compare
Here it is an explanation of differential concept during Tape Era and Veeam Incremental backup against Reverse incremental backup.
More details can be found in this Veeam article.
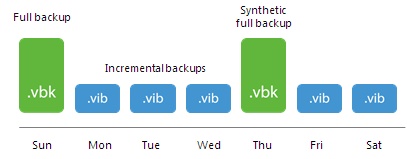
The forward incremental backup with Veeam is the default to write backups on disk. With a forward incremental backup, the virtual machine’s new, unique blocks are transferred to a separate file — the .vib file — after the full backup has been taken (Sunday in the example below). This is repeated with each restore point created, indicated as daily backups in the figure below. One additional technique that is used is the synthetic full backup. This is a great way to reduce the stress on primary storage and still have a complete restore point in one file. The synthetic full backup is created by reading the full backup contained in the .vbk file and the incremental backups to create a full backup file with the contents already in the backup repository. The forward backup is shown below:
Veeam recommends the reverse incremental backup for general-purpose storage, such as holding your backups on a SAN or direct-attached storage devices. The latest restore point is always a full backup file in this example, and the incremental backups are reflected by the previous restore points. The incremental process in this example happens by copying the unique blocks of the VM and then injecting that into the full backup. The blocks that represent the previous restore point are put in a reverse incremental file .vrb that will exist for each restore point in the backup chain. The diagram below shows this process:

[original Veeam article https://www.veeam.com/blog/incremental-vs-differential-backups-which-to-choose.html ]
More details can be found in this Veeam article.

The forward incremental backup with Veeam is the default to write backups on disk. With a forward incremental backup, the virtual machine’s new, unique blocks are transferred to a separate file — the .vib file — after the full backup has been taken (Sunday in the example below). This is repeated with each restore point created, indicated as daily backups in the figure below. One additional technique that is used is the synthetic full backup. This is a great way to reduce the stress on primary storage and still have a complete restore point in one file. The synthetic full backup is created by reading the full backup contained in the .vbk file and the incremental backups to create a full backup file with the contents already in the backup repository. The forward backup is shown below:

Veeam recommends the reverse incremental backup for general-purpose storage, such as holding your backups on a SAN or direct-attached storage devices. The latest restore point is always a full backup file in this example, and the incremental backups are reflected by the previous restore points. The incremental process in this example happens by copying the unique blocks of the VM and then injecting that into the full backup. The blocks that represent the previous restore point are put in a reverse incremental file .vrb that will exist for each restore point in the backup chain. The diagram below shows this process:

[original Veeam article https://www.veeam.com/blog/incremental-vs-differential-backups-which-to-choose.html ]
Multimedia - How to visit most important museum in the world through internet
There are several museum that are on line and visitable.
I am proceeding to mention some of them
I am proceeding to mention some of them
- Rome Vatican Museums: you can take a virtual tour related to museum garden (click here) and Sistina Chapel (click here).
- Louvre virtual tour offer a 360° museum visit (clicca here).
- British museum (click here).
- National Gallery of art (click here).
- Dalì Theatre museum (click here).
- Nasa (click here).
- Smithsonian National museum of natural history (click qui).
- Metropolitan museum of art (click here).
- Google art project (click here). in my opinion one oof the best web tools to visit museum and learnd detailed art production details/explanations
- Uffizi on line http://www.uffizi.com/virtual-tour-uffizi-gallery.asp
- Il museo di Van Gogh at Amsterdam.
- You can visit in High definition several art productions:
http://www.haltadefinizione.com/en/ - As letter website I would likI would like to mention this website:
https://www.artsy.net/
Artsy’s mission is to make all the world’s art accessible to anyone with an Internet connection.
Artsy features the world’s leading galleries, museum collections, foundations, artist estates, art fairs, and benefit auctions, all in one place. Our growing database of 500,000 images of art, architecture, and design by 50,000 artists spans historical, modern, and contemporary works, and includes the largest online database of contemporary art. Artsy is used by art lovers, museum-goers, patrons, collectors, students, and educators to discover, learn about, and collect art.
The National Gallery is currently exhibiting "Michelangelo & Sebastiano", which features Michelangelo Buonarroti.
Michelangelo Buonarroti page provides visitors with Buonarroti's bio, over 20 of his works, exclusive articles, and up-to-date Buonarroti exhibition listings.
The page also includes related artists and categories, allowing viewers to discover art beyond our Buonarroti page.
Labels:
Graphics,
Multimedia
Extra IT - Bed & Breakfast G&G

Today I would like to highlight this Bed & Breakfast that is located nearby Siena:
Here it is relative Facebook link with all details and, from my side, I would like to strongly endorse this location about quality and service quality providing.
https://www.facebook.com/BBGinevra/
City: Capecchio, 139 Lucignano
https://her.is/2nueRr3
https://www.google.it/maps/place/B%26B+Ginevra/@43.238151,11.7610563,17z/data=!3m1!4b1!4m5!3m4!1s0x132be1177e9d9fc9:0x125dde1ab8c02faf!8m2!3d43.238151!4d11.763245
Email: lucia.coradeschi@gmail.com
Labels:
Extra IT
Powershell - Manage AD through Command line
There are several powershell command line to manage or to get Ad information.
To use these feature you need to install some modules depending on your Operative system.
1) Windows 7
These feature is enabled on RSAT module (download Link) and then you need to enable it as follow:
After that you need to launch this command (if you are using old powershell version
Import-Module ActiveDirectory
Precedent command need to be launched everytime. If you want to have it automatically installed you need to , for your account only, add the command Import-Module ActiveDirectory to %UserProfile%\My Documents\WindowsPowerShell\profile.ps1.
If you only want to import the module in the PowerShell console, you would add the above command to Microsoft.PowerShell_profile.ps1.
REMARKS PowerShell command will work only if execution policy is set to RemoteSigned or Unrestricted.
Here it is correct command line:
Set-ExecutionPolicy RemoteSigned


2) Windows 2008 R2 Rsat is already installed and you simple need to enable it like following screenshot.

Import-Module ServerManager
Add-WindowsFeature RSAT-AD-PowerShell
Import-Module ActiveDirectory
To use these feature you need to install some modules depending on your Operative system.
These feature is enabled on RSAT module (download Link) and then you need to enable it as follow:
After that you need to launch this command (if you are using old powershell version
Import-Module ActiveDirectory
Precedent command need to be launched everytime. If you want to have it automatically installed you need to , for your account only, add the command Import-Module ActiveDirectory to %UserProfile%\My Documents\WindowsPowerShell\profile.ps1.
If you only want to import the module in the PowerShell console, you would add the above command to Microsoft.PowerShell_profile.ps1.
REMARKS PowerShell command will work only if execution policy is set to RemoteSigned or Unrestricted.
Here it is correct command line:
Set-ExecutionPolicy RemoteSigned



Import-Module ServerManager
Add-WindowsFeature RSAT-AD-PowerShell
Import-Module ActiveDirectory
Alternatively:
3) Windows 8/8.1 you need only to download RSAT @ 8.0 or RSA @8.1.
All options are enabled by default and nothing more is necessary.
4) Windows 2012 and 2012 R2
You can install from here
or utilizing this command
Add-WindowsFeature RSAT-AD-PowerShell
You do not need to import module.
5) Windows 2016
Through Powershell you can launch these commands:
Get-WndowsFeature RSAT-AD-PowerShell to view if it is installed.
Get-WndowsFeature RSAT-AD-PowerShell to view if it is installed.
Install-WindowsFeature RSAT-AD-PowerShell
Then:
Import-module activedirectory
Get-Module
You will review in Administrative tools --> Active Directory Module for Active directory
6) Windows 10
you can use this script:
https://gallery.technet.microsoft.com/Install-the-Active-fd32e541
RSAT Windows 10
<---------->
You can launch this command line to verify installation went fine
Get-ADUser
You can review all powershell commands available here:
Just to take confidence about potentiality of this commands you can.
Finding Locked-Out Users
Search-ADAccount -LockedOut | where {$_.ObjectClass -eq 'user'} | FT Name,ObjectClass -A
Finding Users Whose Accounts Are About to Expire
The following example demonstrates how to find all the users whose accounts are about to expire in the next 90 days:
Search-ADAccount -AccountExpiring -TimeSpan 90.00:00:00 | where {$_.ObjectClass -eq 'user'} | FT Name,ObjectClass –A
Get-ADUser, which enables you to query information about Active Directory user objects.
To view number of failed logons since the last successful logon for a particular user.
Get-ADUser -Filter {Name -eq "Administrator"} -Properties * | Select-Object Name, msDS-FailedInteractiveLogonCountAtLastSuccessfulLogon
Here it is a Microsoft article that let review all commands that can be useful
Here it is an article that explain some advantages of powershell
More details here:
https://technet.microsoft.com/it-it/library/dd391936(v=ws.10).aspx
[Update 2020.04.29]
If you like to export all AD users you need to use Get-ADUser command using this syntax (it permit you export report in .CSV file)
Get-ADUser -filter * -Properties * | ft Name, saMAccountName, whencreated, LastLogondate, Enabled, Expirationdate, PassowrdExpired, PasswordLastSet, PasswordNeverExpires, Description | Export-CSV C:\TEMP\2020.04.29-ADUsers_1_00.csv -NoTypeInformation -Encoding UTF8
https://morgantechspace.com/2014/10/Powershel-Get-ADUser-Export-Select-Properties-Examples.html
============COMANDO 1 ========
Get-ADUser -filter * -Properties * | ft Name, saMAccountName, whencreated, LastLogondate, Enabled, accountexpirationdate, PasswordExpired, PasswordLastSet, PasswordNeverExpires, Description
============COMANDO 2 ========
Get-ADUser -filter * -Properties * | select Name, saMAccountName, whencreated, LastLogonDate, Enabled, accountexpirationdate, PasswordExpired, PasswordLastSet, PasswordNeverExpires, Description | Measure-Object
============COMANDO 3 ========
Get-ADUser -filter * -Properties * | select Name, saMAccountName, whencreated, LastLogonDate, Enabled, accountexpirationdate, PasswordExpired, PasswordLastSet, PasswordNeverExpires, Description | Export-Csv C:\TEMP\ADUsers_1_01.csv -NoTypeInformation -Encoding UTF8
[Update 2020.04.29]
If you like to export all AD users you need to use Get-ADUser command using this syntax (it permit you export report in .CSV file)
Get-ADUser -filter * -Properties * | ft Name, saMAccountName, whencreated, LastLogondate, Enabled, Expirationdate, PassowrdExpired, PasswordLastSet, PasswordNeverExpires, Description | Export-CSV C:\TEMP\2020.04.29-ADUsers_1_00.csv -NoTypeInformation -Encoding UTF8
https://morgantechspace.com/2014/10/Powershel-Get-ADUser-Export-Select-Properties-Examples.html
============COMANDO 1 ========
Get-ADUser -filter * -Properties * | ft Name, saMAccountName, whencreated, LastLogondate, Enabled, accountexpirationdate, PasswordExpired, PasswordLastSet, PasswordNeverExpires, Description
============COMANDO 2 ========
Get-ADUser -filter * -Properties * | select Name, saMAccountName, whencreated, LastLogonDate, Enabled, accountexpirationdate, PasswordExpired, PasswordLastSet, PasswordNeverExpires, Description | Measure-Object
============COMANDO 3 ========
Get-ADUser -filter * -Properties * | select Name, saMAccountName, whencreated, LastLogonDate, Enabled, accountexpirationdate, PasswordExpired, PasswordLastSet, PasswordNeverExpires, Description | Export-Csv C:\TEMP\ADUsers_1_01.csv -NoTypeInformation -Encoding UTF8
Hacker - Wifi without password and DNS Spoofing/Arp Poisoning
Wifi without password has higher risk than usually known from non IT persons and underestimated as problem as well.
You need consider that website to IP translation is done, obviously, from DNS server and DNS Spoofing technique (with ARP poisoning) that change website name to IP association.
In this way, with Pishing technique, a website cloning is proposed to user that write on browser, for example, www.facebook.com.
So hacker can get user and password insertion and stole, in this way, user credentials.
If you like you can read this italian article that explain more verbosely concept.
http://www.matematicamente.it/informatica/11535-dns-spoofing-e-phishing-rischi-per-wifi-non-protetta
[update 2019.06.01]
Today I would like to indicate risks about WIFI SSID properly created to collect information, passwords and so on.
https://pixelprivacy.com/resources/public-wifi-dangers/
You need consider that website to IP translation is done, obviously, from DNS server and DNS Spoofing technique (with ARP poisoning) that change website name to IP association.
In this way, with Pishing technique, a website cloning is proposed to user that write on browser, for example, www.facebook.com.
So hacker can get user and password insertion and stole, in this way, user credentials.
If you like you can read this italian article that explain more verbosely concept.
http://www.matematicamente.it/informatica/11535-dns-spoofing-e-phishing-rischi-per-wifi-non-protetta
[update 2019.06.01]
Today I would like to indicate risks about WIFI SSID properly created to collect information, passwords and so on.
https://pixelprivacy.com/resources/public-wifi-dangers/
Tips - Copy and paste - CTRL+C and CTRL+V under Windows 10
Inside windows 10 there is a simple tip that help you to enable copy and paste on command prompt windows.
here is relative screenshot that is decisively verbose.

here is relative screenshot that is decisively verbose.

Labels:
Scripting,
Tips,
Windows 10
Veeam Explorer for Active Directory and Group policy Object Restore procedure
Today I would like to mention Veeam Explorer for Microsoft Active Director released with Veeam Backup & Replication versions v9 and 9.5
Veeam Explorer for Microsoft Active Directory was a part of Veeam Backup & Replication v8. Its initial functionality was intended to solve the most frequent cases administrators have with Active Directory: Granular objects and containers recovery (ok, password recovery also was included, as well as AD data export in LDIFDE format)
Starting from Veeam Backup & Replication v9, you can restore Group Policy Objects, and the process is very easy.
About domain controller backup you can review this veeam article:
https://www.veeam.com/blog/backing-up-domain-controller-best-practices-for-ad-protection.html
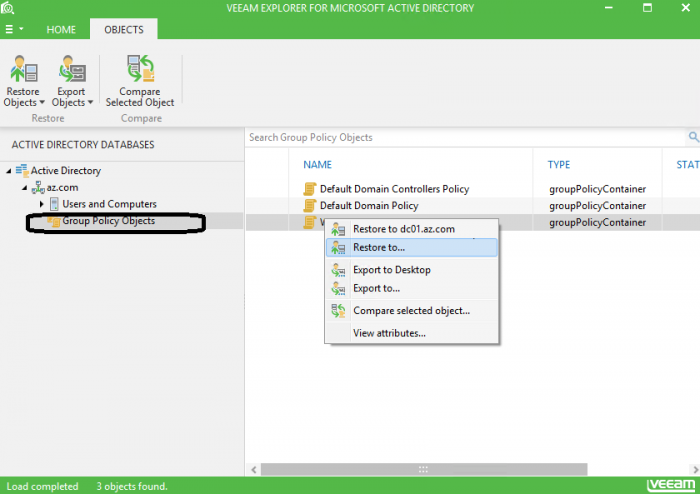
Group policy restore follow this step by step procedure:
The actual recovery procedure is very similar to one I described before:
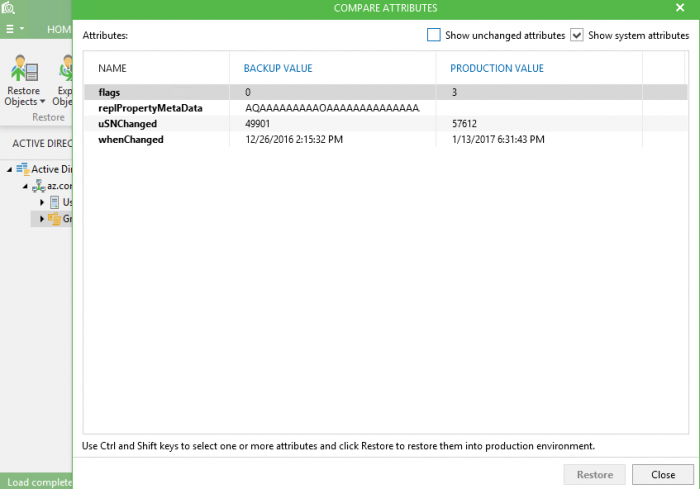
Hint: As an option, the administrator can compare GPO attributes with the production state and see what exactly was changed (figure 2).
Additional improvements to Veeam Explorer for Microsoft Active Directory
Besides that, in the same version 9, Veeam Explorer for Microsoft Active Directory added support for the recovery of:
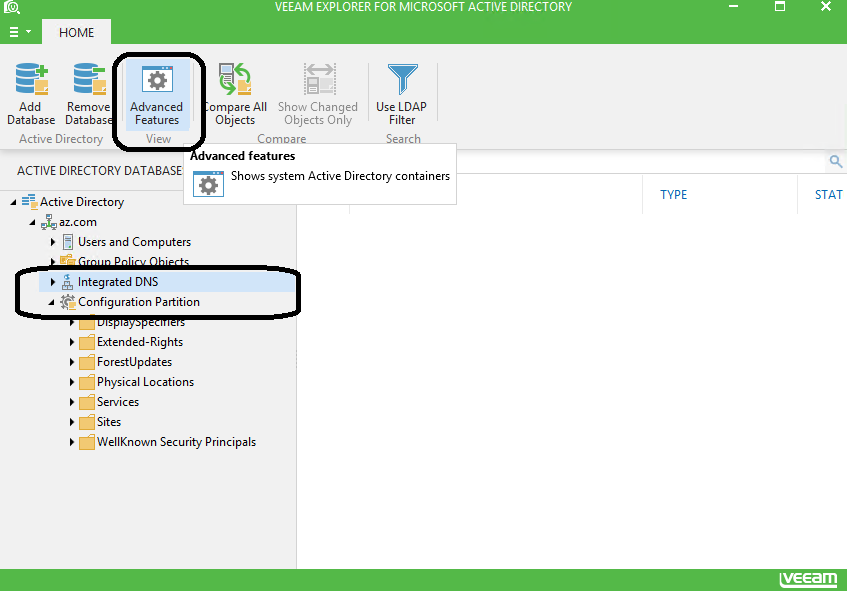
Active Directory-integrated DNS records (DNS integrated into Active Directory and replicated as a part of Domain Services replication)
Objects in Active Directory configuration partition (Native AD partitions containing forest-wide information about existing domains and sites available services, which come per forest and are replicated to all Domain Controllers)
https://www.veeam.com/blog/how-to-recover-group-policy-objects.html
Veeam Explorer for Microsoft Active Directory was a part of Veeam Backup & Replication v8. Its initial functionality was intended to solve the most frequent cases administrators have with Active Directory: Granular objects and containers recovery (ok, password recovery also was included, as well as AD data export in LDIFDE format)
Starting from Veeam Backup & Replication v9, you can restore Group Policy Objects, and the process is very easy.
About domain controller backup you can review this veeam article:
https://www.veeam.com/blog/backing-up-domain-controller-best-practices-for-ad-protection.html
Group policy restore follow this step by step procedure:
The actual recovery procedure is very similar to one I described before:
- Administrator starts application-item restore for Microsoft Active Directory from the main ribbon or via the backups hive
- Then, the administrator selects an appropriate backup point with a known valid state
- Veeam Backup & Replication mounts that restore point to the backup server, extracting the Active Directory database and SYSVOL catalog, and automatically opens them in Veeam Explorer for Microsoft Active Directory
- If all prerequisites are met, the administrator should be able to find the Group Policy Objects container right below the Users and Computers container
- Then, the administrator finds a desired GPO manually or by using the search, and performs either the restore or export procedure (figure 1)

Hint: As an option, the administrator can compare GPO attributes with the production state and see what exactly was changed (figure 2).

Additional improvements to Veeam Explorer for Microsoft Active Directory
Besides that, in the same version 9, Veeam Explorer for Microsoft Active Directory added support for the recovery of:
Active Directory-integrated DNS records (DNS integrated into Active Directory and replicated as a part of Domain Services replication)
Objects in Active Directory configuration partition (Native AD partitions containing forest-wide information about existing domains and sites available services, which come per forest and are replicated to all Domain Controllers)

Additional resources:
Note: Group Policy is a Windows Server feature (since Windows Server 2000) that allows an administrator to centrally manage the working environment of users and computers, allowing common policies to be configured from one place and then distributed at ease, while also controlling what users/computers can or cannot do.https://www.veeam.com/blog/how-to-recover-group-policy-objects.html
Subscribe to:
Posts (Atom)

